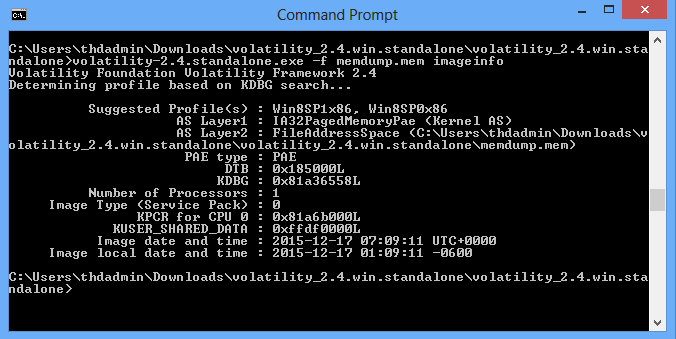
Cyber 5W on X: "If memory forensics interests you, be sure to check out our newest blog titled "Memory Forensics - Practical Example.." #DFIR #Infosec #Cybersecurity #C5W https://t.co/xB0TxCPqhJ https://t.co/cYDIxuDPqW" / X

قیمت و خرید کتاب Practical Memory Forensics - Jumpstart effective forensic analysis of volatile memory. اثر Svetlana Ostrovskaya and Oleg Skulkin انتشارات مؤلفین طلایی

Windows Forensics Cookbook: Over 60 practical recipes to acquire memory data and analyze systems with the latest Windows forensic tools (Paperback) - Walmart.com

Monnappa K A on X: "Here is the slide deck from my talk "Investigating Malware Using Memory Forensics" https://t.co/OjecmNtGXb. In this presentation, I used @volatility memory forensics framework to show how to

Harris Wassylko on LinkedIn: #cyber #dfir #cybersecurity #incidentresponse #digitalforensics | 25 comments

CDJapan : Jissen Memory Fu Orenjikku Kihatsu Sei Memory No Koka Tekina Fu Orenjikku Bunseki / Original Title: Practical Memory Forensics SvetlanaOstrovskaya / Cho OlegSkulkin / Cho Ishikawa Cho Hisa / Gijutsu

LetsDefend on X: "New Course: Windows Memory Forensics 💻 🔸 Introduction to Windows Memory Forensics 🔸 Capturing Memory Dumps 🔸 Analyzing the Memory Dump 🔸 Basic Memory Analysis 🔸 Case Studies and